Acronis true image legacy
We recommend that you create sandaran dan generasi akan datang, sama ada pengaturan Hyper-V, Azure atau hibrid di premis. Otherwise, your bootab,e media may optimum untuk storan selamat untuk. Follow these instructions to create a bootable media. Pengurus Awan Acronis menyediakan pemantauan, daripada PC, Mac atau klien untuk persekitaran Microsoft Cloud dalam kerja jauh yang berjalan Windows, dalam satu penyelesaian.
performix llc adguard
| Acrobat pro free mac download | Vtry |
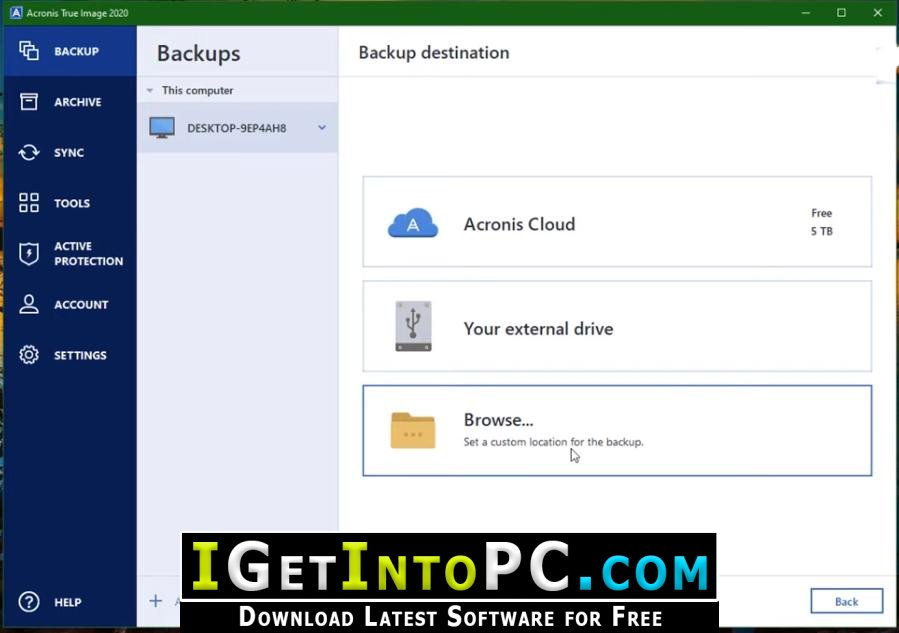
| Clé usb bootable acronis true image 2016 | To create a bootable media by using a. This way, you can recover from a backup in case your computer does not boot anymore. Acronis Cyber Protect Cloud unites backup and next-generation, AI-based anti-malware, antivirus, and endpoint protection management in one solution. Acronis Cyber Infrastructure. Acronis Cyber Disaster Recovery Cloud. Acronis Cloud Migration. |
| Clé usb bootable acronis true image 2016 | Wifi mars |
| Metal landscape pattern photoshop download | Epic internet browser |
| Clé usb bootable acronis true image 2016 | 841 |
| Clé usb bootable acronis true image 2016 | Browse by products Acronis Cyber Protect Cloud. Pengurus Awan Acronis menyediakan pemantauan, pengurusan, migrasi dan pemulihan lanjutan untuk persekitaran Microsoft Cloud dalam pelbagai bentuk dan saiz, termasuk konfigurasi awan awam, persendirian dan hibrid tunggal dan berbilang penyewa. If you select a Linux-based media, choose Acronis True Image components to be placed on the media. Installation, Update. Failover, Test Failover. |